Welcome to August! The latest Patch Tuesday update dropped yesterday, releasing updates for 107 vulnerabilities. and fixing 1 publicly disclosed vulnerability.
Pssst... did you know that you can now set up AutoFix rules for Windows Updates with RoboShadow's Cyber Heal function?
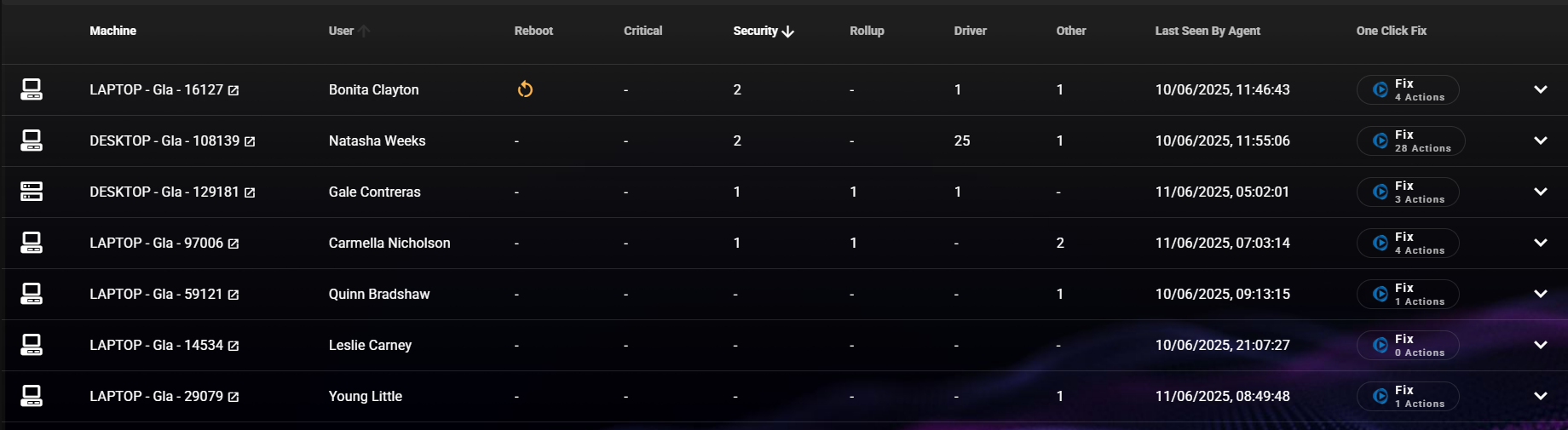
You can find a full list of security updates for August here.

Key Updates
- 107 Vulnerabilities Patched
- 1 publicly disclosed zero-day
- 13 critical vulnerabilities
Vulnerability Types Released in August 2025:
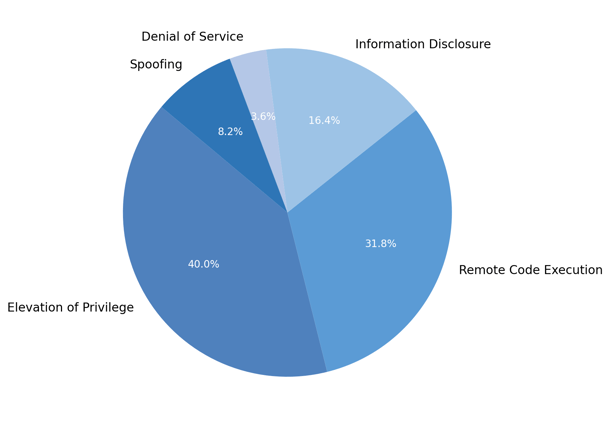
Zero Day Vulnerabilities
CVE-2025-53779 – Windows Kerberos Elevation of Privilege
Critical Vulnerability Summary
The following critical CVEs have been remediated this month, and should be patched as soon as possible:
| CVE |
CVSS |
Description Summary |
| CVE-2025-50165 |
9.8 |
RCE in Windows graphics via JPEG decoding without user interaction
|
| CVE-2025-53766 |
9.8 |
GDI+ RCE via heap overflow using malicious metafiles, no user interaction needed |
| CVE-2025-53778 |
8.8 |
NTLM EoP bug allowing SYSTEM-level elevation over network; exploitation more likely |
| CVE-2025-53740 |
8.4 |
Use-after-free RCE in Microsoft Office (Preview Pane) |
| CVE-2025-53731 |
8.4 |
Use-after-free RCE in Microsoft Office (Preview Pane) |
| CVE-2025-53784 |
8.4 |
Use-after-free RCE in Microsoft Word (Preview Pane) |
| CVE-2025-53733 |
8.4 |
RCE in Microsoft Word via numeric conversion error (Preview Pane) |
| CVE-2025-50177 |
8.1 |
MSMQ RCE via use-after-free and race condition exploiting HTTP packets |
| CVE-2025-49707 |
7.9 |
Azure VM spoofing via improper access control |
| CVE-2025-50176 |
7.8 |
RCE in DirectX Graphics Kernel via type confusion |
| CVE-2025-53781 |
7.7 |
Azure VM information disclosure by low-privilege attacker |
| CVE-2025-53793 |
7.5 |
Azure Stack Hub information disclosure |
| CVE-2025-48807 |
7.5 |
RCE in Hyper-V—nested VM escape to guest admin |

Actions to Take:
Here is what IT teams should prioritise this month:
-
Patch Immediately: Immediately deploy fixes for CVE-2025-50165, CVE-2025-53766, and CVE-2025-53778, as these have the highest CVSS scores and/or are more likely to be exploited. Also apply the patch for CVE-2025-53779 (Windows Kerberos EoP zero-day) without delay, even though exploitation is currently considered less likely.
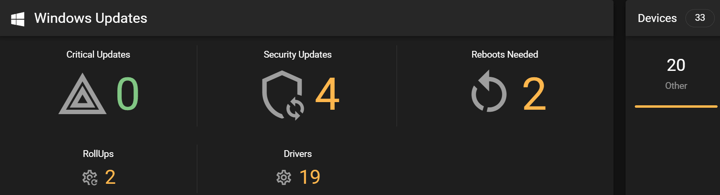
-
Update All Systems Running Office and Word: The multiple use-after-free RCE vulnerabilities in Microsoft Office and Word can be triggered via the Preview Pane, meaning a malicious document can execute code without being opened. Disable the Preview Pane where patching is not yet complete.
-
Patch Internet-Facing Systems First: Apply updates to all public-facing servers and services before internal systems, especially Azure VMs, Hyper-V hosts, and DirectX-enabled systems.4
-
Audit and Monitor Kerberos and NTLM Traffic: For CVE-2025-53779 and CVE-2025-53778, review authentication logs for unusual patterns, failed login bursts, or unexpected privilege escalations.

Did you know? You can use the RoboShadow platform to scan for vulnerabilities, check your Windows Updates and also patch any outstanding software updates using Cyber Heal?
If you have any questions about Patch Tuesday, or feedback on this blog please
reach out to us: hello@roboshadow.com
Thanks for reading!