Patch Tuesday: June 2025
As we ease into the summer months in the UK (Spoiler - it's still cloudy!), so have Microsoft. June's Patch Tuesday has released a relatively modest 67 security fixes. While that might be good news for IT admins, it’s no time to fully relax, with 2 zero-days being actively exploited and 10 critical updates.
This comes at the same time that RoboShadow has added Windows Updates into our Cyber Heal portfolio, with Autofix to follow very soon!
You can find a full list of security updates for June here.

Key Updates
- 6 Vulnerabilities Patched
- 1 Actively Exploited Zero Day Vulnerability and 1 previously disclosed
- 10 critical vulnerabilities.
Vulnerability Types Released in June 2025:

Zero Day Vulnerabilities
CVE-2025-33053 – WebDAV Remote Code Execution
- CVSS Score 8.8 (High)
- Description: This vulnerability arises from improper validation in the WebDAV client, which can allow an attacker to remotely execute code on a target system. By tricking a user into interacting with a malicious WebDAV share, attackers can cause a legitimate Windows executable (like
iediagcmd.exe) to run malicious payloads. - Exploitation Status: This flaw is actively being exploited in the wild, with Microsoft attributing attacks to the Stealth Falcon APT group targeting government entities in the Middle East. It has also been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
- Fix: Microsoft addressed this in the June 2025 Patch Tuesday release. Users are strongly advised to apply the update immediately. Organizations should also consider blocking outbound WebDAV traffic and disabling handling of
.urlfiles over WebDAV as a precaution.
CVE-2025-33073 – Windows SMB Client Elevation of Privilege Vulnerability
- CVSS Score: 8.8 (High)
- Description: This vulnerability affects the Windows SMB client and could allow a low-privileged attacker to escalate privileges to SYSTEM. The flaw can be exploited by enticing a target to connect to a malicious SMB server, effectively enabling remote privilege escalation.
- Exploitation Status: Although there are no reports of active exploitation, the vulnerability has been publicly disclosed, and proof-of-concept code is available.
- Fix: Microsoft patched this vulnerability in the June 2025 updates. Administrators should prioritize applying the update and consider enabling SMB signing to mitigate similar attack vectors in the future.
Critical Vulnerability Summary
This April, Microsoft released fixes for 11 Critical Vulnerabilities.
- CVE-2025-47172 – SQL injection vulnerability in SharePoint
CVSS Score: 8.8
Description: An attacker could exploit a flaw in SharePoint's SQL handling to achieve remote code execution. - CVE-2025-47167 – Type confusion issue in Microsoft Office
CVSS Score: 8.4
Description: Exploitation requires no user interaction once a malicious file is previewed, making it a silent threat. - CVE-2025-47164 – Use-after-free vulnerability in Office allowing code execution on a local system.
CVSS Score: 8.4
Description: Triggers through crafted Office documents; no special privileges required. - CVE-2025-47162 – Heap buffer overflow in Office potentially enabling local code execution.
CVSS Score: 8.4
Description: A specially crafted file can corrupt memory, enabling arbitrary code execution. - CVE-2025-47953 – Use-after-free vulnerability in Office that could be leveraged for local code execution.
CVSS Score: 8.4
Description: Similar to CVE-2025-47164, but targets a different code path in Office file handling. - CVE-2025-33071 – Use-after-free in the Windows KDC Proxy Service.
CVSS Score: 8.1
Description: Exploitable over the network, allowing code execution within the context of the KDC proxy. - CVE-2025-33070 – Initialization flaw in Netlogon that could allow remote privilege escalation.
CVSS Score: 8.1
Description: Attackers could elevate privileges via crafted Netlogon requests. - CVE-2025-32710 – Race condition in Remote Desktop Services enabling RCE under specific conditions.
CVSS Score: 8.1
Description: Complex to exploit but potentially severe in high-value environments. - CVE-2025-29828 – Memory handling flaw in Cryptographic Services used by TLS and related components.
CVSS Score: 7.8
Description: Could lead to code execution or service crashes under crafted input scenarios.
Actions to Take:
With two zero-days in the wild and several critical vulnerabilities affecting core Windows and Office components, here’s what IT teams should prioritise this month:
-
Patch Immediately
-
Apply the June 2025 updates across all systems, especially for:
-
CVE-2025-33053 (WebDAV RCE) – actively exploited zero-day.
-
CVE-2025-33073 (SMB Client EoP) – publicly disclosed with PoC.
-
All Office-related RCE vulnerabilities (47164, 47167, 47162, 47953).
-
SharePoint CVE-2025-47172 – critical SQL injection.
-
-
-
Harden Network Protections
-
Consider blocking outbound WebDAV traffic and restricting
.urlfile handling via Group Policy or endpoint protection platforms. -
Enable SMB signing where applicable to mitigate potential lateral movement from SMB-based exploits.
-
-
Prioritise High-Risk Assets
-
Focus patching efforts on internet-facing services, critical servers (including SharePoint), and executive/privileged endpoints.
-
-
Audit & Monitor
-
Review logs for unusual WebDAV or SMB activity.
-
Watch for connections to untrusted file shares or use of legacy protocols.
-
-
Enable AutoFix (if using RoboShadow)
-
With Windows Updates now part of the Cyber Heal portfolio, enabling AutoFix (once live) will help automate patch deployment and reduce exposure windows going forward.
-
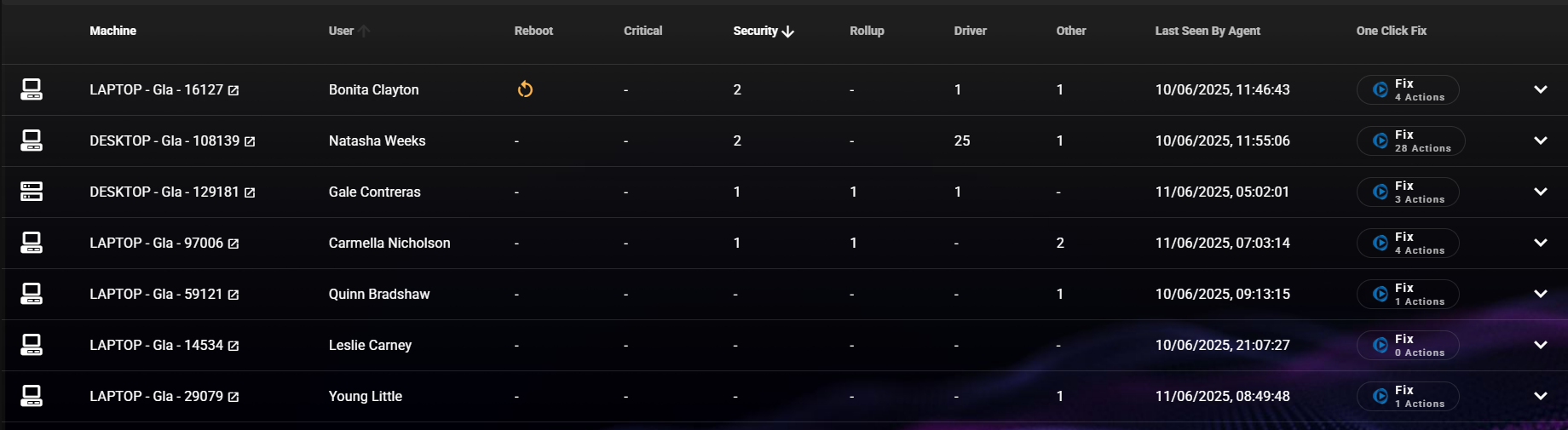
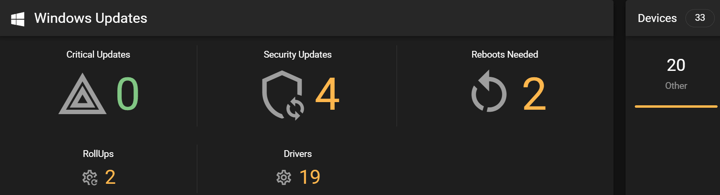
Did you know? You can use the RoboShadow platform to scan for vulnerabilities, check your Windows Updates and also patch any outstanding software updates using Cyber Heal.
If you have any questions about Patch Tuesday, or feedback on this blog please
reach out to us: hello@roboshadow.com
Thanks for reading!


