Patch Tuesday: November 2025
With the year winding down, November’s Patch Tuesday brings a lighter load from Microsoft: 63 security fixes in total, including one actively exploited zero-day vulnerability. While the volume is smaller, the impact of this update shouldn’t be overlooked. In this blog, we break down the most important patches and outline how you can stay ahead of potential risks.
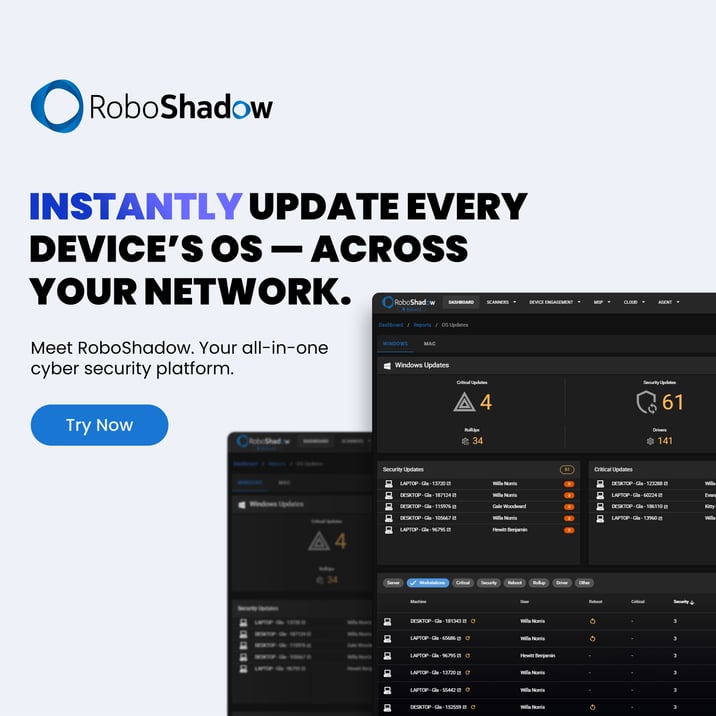
Pssst, as a reminder... did you know that you can now set up AutoFix rules for Windows Updates with RoboShadow's Cyber Heal function?
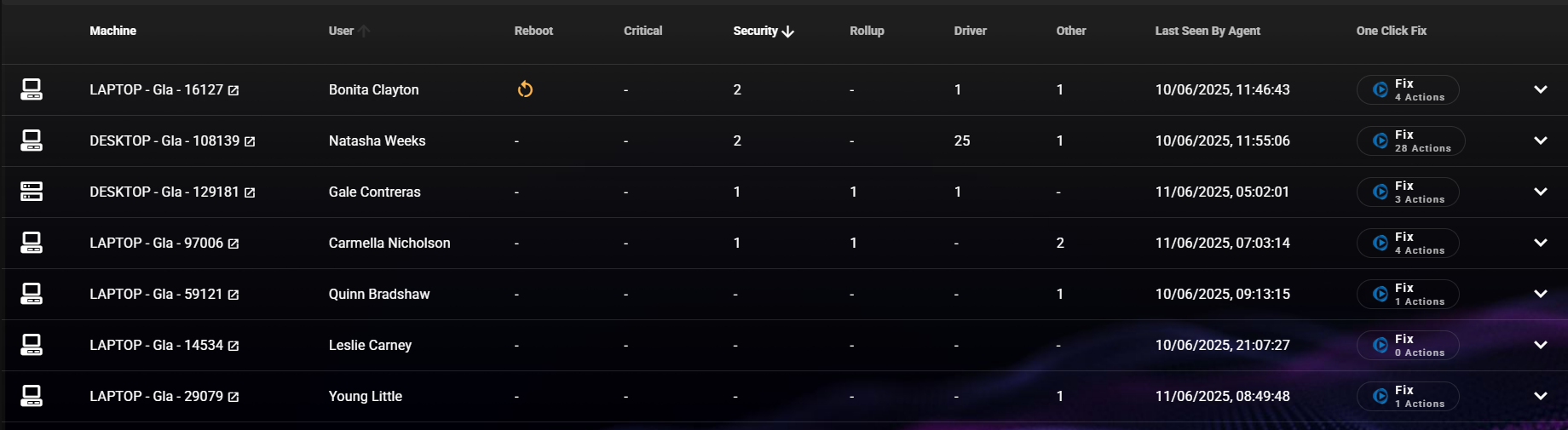
You can find a full list of security updates for November here.

Key Updates
- 63 Vulnerabilities Patched
- 1 publicly disclosed zero-day
- 4 critical vulnerabilities
Vulnerability Types Released in November 2025:

Zero Day Vulnerabilities
CVE-2025-62215 — Windows Kernel Elevation of Privilege
-
CVSS Score: 7.0 (High)
-
Description: A race-condition (concurrent execution using a shared resource with improper synchronization) in the Windows Kernel can allow a local, authenticated attacker to elevate privileges to SYSTEM. Successful exploitation requires winning the race condition; Microsoft’s published description matches the CWE for improper synchronization
-
Impact: Because this is a kernel-mode privilege escalation, a successful exploit lets an attacker gain SYSTEM privileges, enabling persistence, disabling protections, and facilitating lateral movement.
- Remediation: Microsoft released a patch as part of the November 2025 updates; affected systems should be patched and rebooted promptly. Prioritize hosts with elevated exposure (admin workstations, jump boxes, RDP/VDI hosts, domain controllers) and validate install status via your update management tooling.
Critical Vulnerability Summary
Here are some of the critical CVEs that have been remediated this month, and should be patched as soon as possible:
| CVE ID | CVSS | Description Summary |
|---|---|---|
| CVE-2025-62199 | 9.8 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability. Successful exploitation could allow an attacker to execute arbitrary code remotely via specially crafted network packets. |
| CVE-2025-30398 | 9.8 | Microsoft Office Word Remote Code Execution Vulnerability. Attackers can exploit this issue through malicious Word documents to gain the same user rights as the logged-in user. |
| CVE-2025-62214 | 9.6 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability. Exploitation could allow code execution through specially crafted network traffic. |
| CVE-2025-60716 | 9.0 | Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability. An authenticated attacker could execute arbitrary code by sending malicious requests to a vulnerable Dynamics service endpoint. |
Actions to Take:
With November’s smaller patch batch, now’s a good opportunity to tighten up patch management and focus on prioritisation. Here’s where to start:
-
Prioritise the zero-day (CVE-2025-62215): Deploy the Windows Kernel update across all supported systems as soon as possible. Since this vulnerability is already being exploited, it should take top priority.
-
Address all critical RCEs quickly: The MSMQ, Microsoft Word, and Dynamics 365 vulnerabilities (CVE-2025-62199, CVE-2025-30398, CVE-2025-62214, and CVE-2025-60716) pose the highest risk of remote exploitation. Patch or isolate affected systems promptly.
-
Audit high-value assets: Confirm that domain controllers, servers, and administrative workstations are fully up to date and running supported configurations.
-
Validate patch deployment: Don’t assume compliance—verify it. Use vulnerability management tools like RoboShadows to confirm that updates have successfully applied and that residual exposure is minimal.
-
Review and reinforce least-privilege policies: Since this month’s active exploit targets privilege escalation, double-check local admin rights and service account permissions.
-
Schedule controlled reboots: Many of these patches affect kernel components and drivers. Make sure to plan for reboots to fully apply changes.
Final Thought:
November’s Patch Tuesday may be lighter, but it still carries weight. The single actively exploited zero-day shows how attackers continue to target privilege escalation and quiet persistence inside networks.
As the year wraps up, it’s worth taking stock of patch routines, verifying coverage, and ensuring critical systems are in good shape for 2026. A steady, reliable patching rhythm and clear visibility through tools (like RoboShadow!) can make staying secure feel a lot more manageable.
If you have any questions about Patch Tuesday, or feedback on this blog please
reach out to us: hello@roboshadow.com
Thanks for reading!