Vulnerability Scanning & Management Platform
The RoboShadow platform allows companies, institutions, and individuals to get an internal and external 'Vulnerability Assessment' daily.
With Cyber Heal AutoFix, vulnerabilities identified by RoboShadow are automatically remediated, reducing risk faster and simplifying patch management.

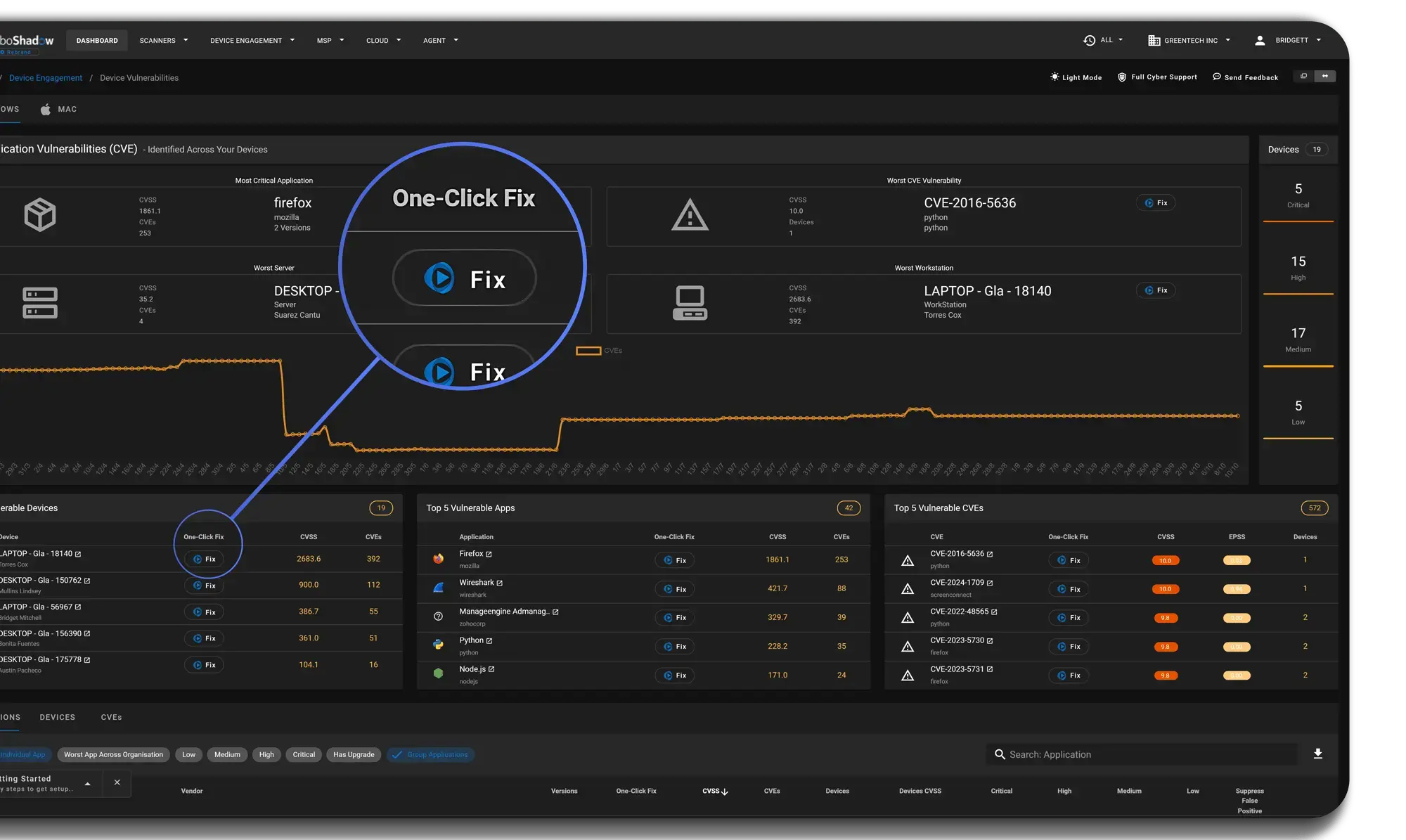
Automated Vulnerability Remediation
Remove 80% of Remediation via Automation
Using our Cyber Heal technology, our AutoFix process remediates issues across the estate automatically whilst updating your PSA / Help Desk System .- Remediate vulnerabilities across 7,000+ applications from Microsoft Winget Repository
- Rapidly uninstall unwanted or unsecure applications.
- Apply custom patches using your own MSIs / EXEs.
- Enforce security benchmarks to align with compliance standards.
- Update Firewall and Anti-Ransomware settings.
- Automate vulnerability remediation in the background with AutoFix.
- Log any AutoPilot fails into your Service Desk System / PSA for a follow-up.
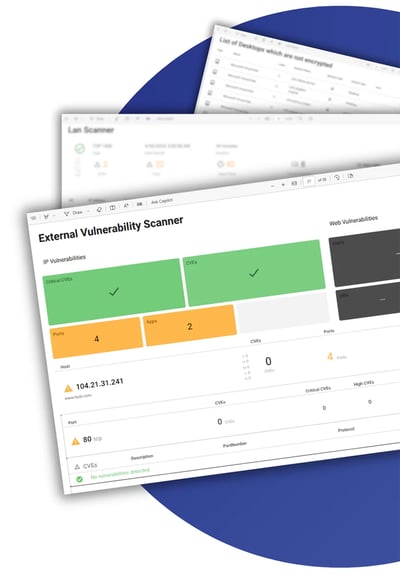
No Vulnerability Left Behind: External Vulnerability Scanning
The External 'Attack Surface' Scanner

Simply enter your IP Addresses & Websites, and access a dashboard that gives you a full External Vulnerability Scan of vulnerable ports, IPs, CVEs, and Website Vulnerabilities. From this dashboard, you can easily monitor and prioritise your top vulnerabilities so you know what needs immediate attention.
Our system automatically scans and sends results directly to your email every day.
%20HD%20png-1.webp)
Find the Weak Link in Your Network Security.
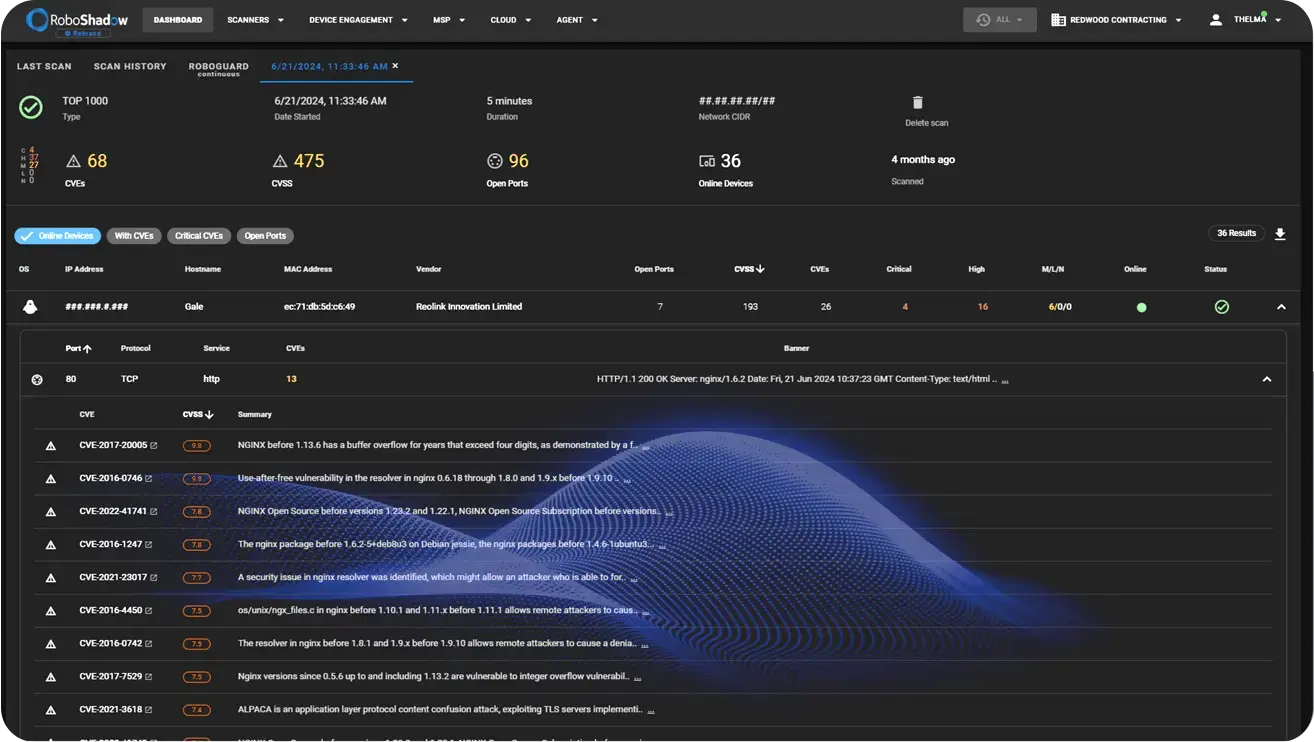
LAN scanner
The RoboShadow LAN Scanner performs full network vulnerability scanning on your internal environment. It discovers every connected device and runs a detailed vulnerability assessment across your subnet, highlighting exposed IoT, endpoints, and misconfigured equipment.
The scanner helps you understand and manage your internal attack surface and covers the following scenarios:
- What vulnerable IoT devices could a hacker hide in?
- Are your networks open (flat), or are they properly segregated?
- Which network equipment has exploitable vulnerabilities?


LAN Scanner
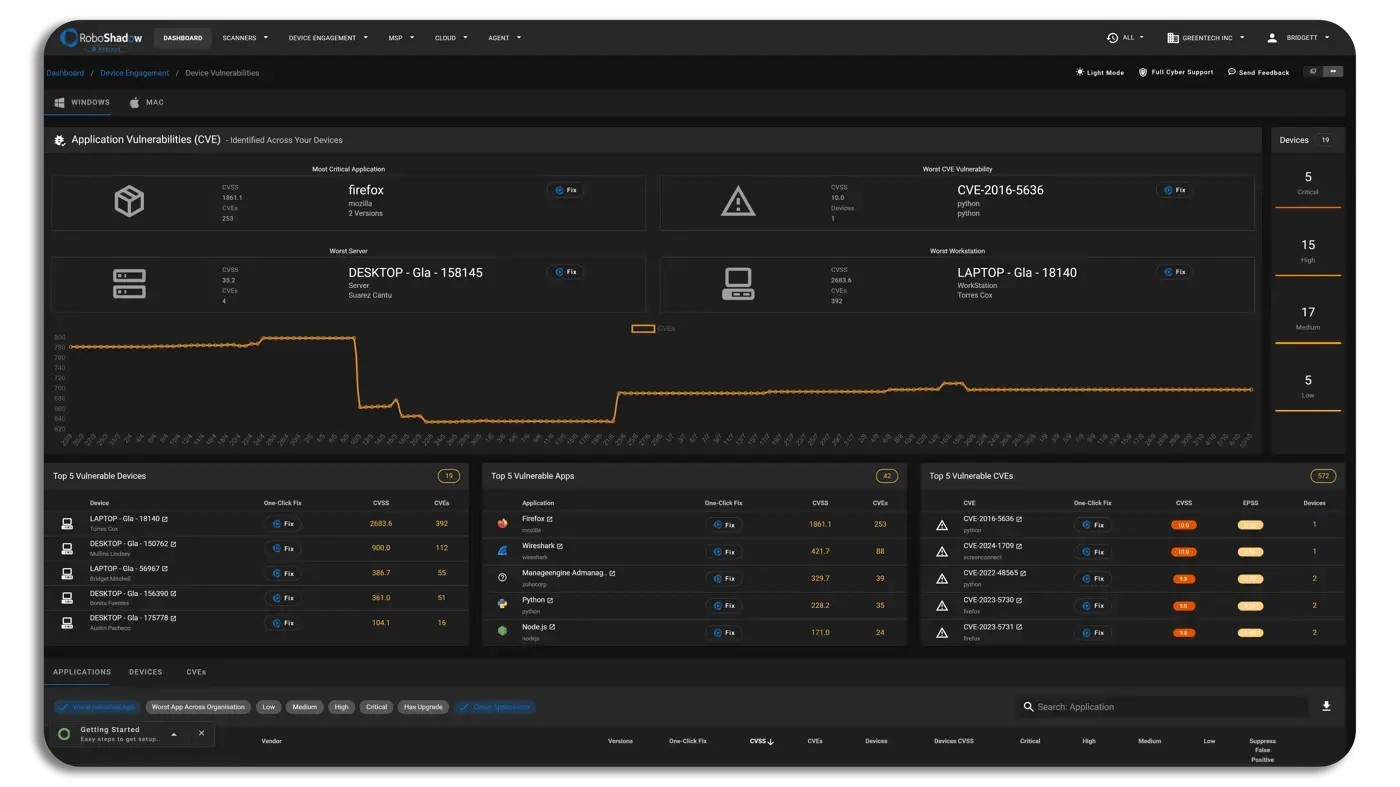
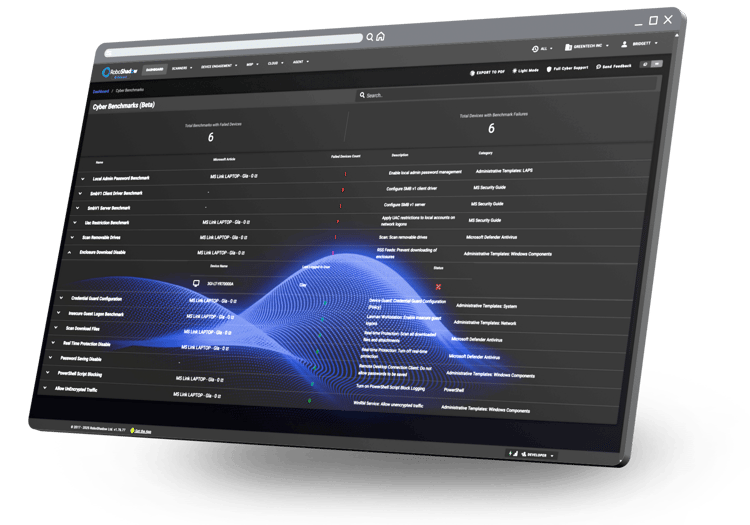
Strengthen Your Defenses with Real-Time Vulnerability Monitoring
The 'Zero Trust' Approach to continuous security and risk management.
Detailed insights into key Zero Trust counters: Device Vulnerabilities, Antivirus Status, OS Updates, Benchmarks & Config, Encryption Status, Hardware Information, and Software Patching.
By combining real time vulnerability monitoring with automated patch and update management, our platform ensures your endpoints stay secure and compliant against evolving threats.
%20(2).png?width=500&height=83&name=Add%20a%20heading%20(5000%20x%204322%20px)%20(2).png)
Device Vulnerabilities

Anti-Virus

OS Updates

Device Encryption
Misconfigured systems can be just as dangerous as known exploits. RoboShadow continuously evaluates your environment against industry security benchmarks, helping you identify weak configurations and reduce risk.
By combining configuration hardening with ongoing vulnerability assessments, our platform ensures your organisation stays aligned with compliance frameworks and Zero Trust policies.
This proactive approach strengthens your vulnerability management strategy by closing gaps before attackers can exploit them.
Cyber
Community
Our Free Tier is named as "Worlds best Cyber Free Tier" as 90% of our product is included. We provide you with the tools to be able to successfully manage and enhance your security.
£0
- External IP Attack Surface Scan
- Website Security Scanner (OWASP)
- Windows CVE Reporting
- Integrate fully with 365
Cyber
Professional
All Community features plus AI tech, continuous scanning, 1-click fixes, Shodan integration, attack mapping, and priority scans. £20/month , £1 per agent
£20 / mo + £1 per agent
- Cyber Heal ‘AutoFix' (£1 per agent)
- RoboGuard Vulnerability Alerting'
- PSA & Ticket Integration
- Realtime Agent Reporting
Cyber
Enterprise
Includes all features of 'Cyber Professional' plus an advanced governance team layer, specifically designed for higher-level teams requiring enhanced oversight and management capabilities.
£200 / mo
- Account Manager
- Cyber Governance Support
- Yearly Penetration Test Support
Seamless PSA Ticketing Integrations
for Total Cybersecurity Control.
RoboShadow integrates with Zendesk, Jira, Windows Defender, Malwarebytes, CrowdStrike, ServiceNow and more!

Continuous Cyber Scanning
Continuously Scan your attack surface every day and get alerts with any new vulnerabilities.
Meet your obligations for various Cyber Frameworks to demonstrate you perform continuous vulnerability scanning across your entire estate.
.webp)
'Stand Alone' Tools Within The Platform.
MFA
MFA is the "lowest hanging fruit to attack.” That's why robust MFA Auditing is crucial.Our MFA Non-Conformance Report tracks compliance, including:
❍ Guest User MFA Reporting
❍ Global Admins Compliance
❍ Update Reboot Reporting
❍ Azure AD Reconciliation
-1.png)
Domain Enumeration
The Domain Enumeration feature allows users to quickly identify all subdomains and backend systems associated with their main business domain, highlighting potential security risks.
By scanning these often-overlooked areas, users can gain insights into assets that may be vulnerable to attack, such as test environments and staging servers. This free tool in RoboShadow’s platform empowers businesses to secure their digital infrastructure more effectively and proactively.
.png?width=2000&height=1230&name=Add%20a%20heading%20(17).png)
As Seen On YouTube
like. Comment. Subscribe.
@RoboShadow • 2.91k Subscribers • 51 videos
Through YouTube, we can connect with our community and provide in-depth tutorials on getting the most out of RoboShadow. If you have any questions or suggestions for video content, feel free to reach out to us at Hello@roboshadow.com.
What Our Clients Say...
-
"Many more clients are being asked by their clients and insurance companies for evidence that they are conducting regular vulnerability scanning, and RoboShadow makes it super easy to run scans on our client networks, resolve issues, and produce lovely-looking reports for our clients."
.png?width=50&height=50&name=Untitled%20design%20(34).png)
Aaron Nihat
-
"RoboShadow is super quick to setup and cost effective Cyber management."

Manny, 3GV
-
"The RoboShadow platform allows us to keep tabs on our External Attack Surface."

Ben, Crank
-
"An essential security and analysis tool… I use it every day!"

Bernie, Ultumus
-
"The Robo Shadow platform worked wonders for our Penetration Testing."

Kevin, Hotwire
-
"Responsive, friendly and cost-effective security solutions. I'd happily recommend them to industry peers."

David
Around the world, we all have different ways of proving our Cyber Security posture. For many businesses, using a good governance framework is a great way of proving to your customers, regulators, and investors how seriously you take your cyber governance.
RoboShadow has a compliance engine built within the platform, allowing you to export evidence data for a whole host of cyber governance frameworks including but not limited to:
• Cyber Essentials (UK)• Essential 8 (Australia)
• NIST (US)
• SOC 2 (Worldwide)
• ISO 27001 (Worldwide)
• HIPAA (US)
.png)


-png-1.png?width=70&height=70&name=MicrosoftTeams-image%20(53)-png-1.png)
.png?width=2000&height=1226&name=Add%20a%20heading%20(18).png)