How to Check Open Ports on External Network Devices
Open ports on your external networks are an easy access point for bad actors to exploit, and any security conscious company will ensure that no external ports are left open.
All penetration tests and vulnerability scanners will mark you down for open ports. It is important to know how to check open ports on your external network devices, and what to do with them if you find them.
Identifying and querying open ports is essential to prevent unauthorized access, maintain a robust network, and protect sensitive data. In this blog, we'll walk you through the process of querying open ports found on external network devices.
Identifying Open Ports
Before we delve into the process of querying open ports, let's first understand how to identify them. There are several open port checker tools available to scan your network for open ports. Some popular options include Nmap, Zenmap (the graphical user interface for Nmap), and Port Scanner by SolarWinds.
You can also use RoboShadow's external vulnerability scanner for FREE to detect open ports and other threats on both your external network.
These tools enable you to scan IP addresses, individual devices, and subnets connected to your external networks. Once the scans are complete, you will be able to see a complete list of open ports on your networks and can begin the process of closing them!
How to use RoboShadow to Detect Open Ports for FREE
This quick guide explains how to use the RoboShadow Web Platform to perform an external vulnerability scan. Using our free online tool, you can easily run an NMAP scan to identify your open ports.
Head to the RoboShadow Portal, and click on External Scanner to get started.
Step 1: Input your External IP address into the IP address field.
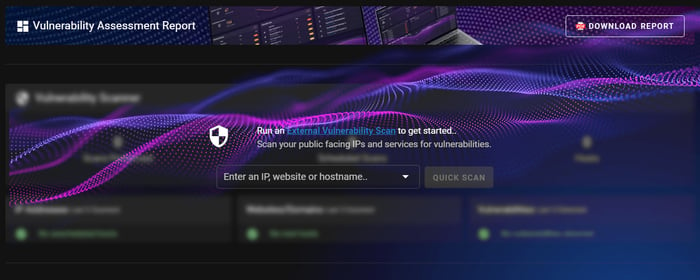
Step 2: Select 'NMap' (as well as any other type of scan you need), then press 'START'
![]()
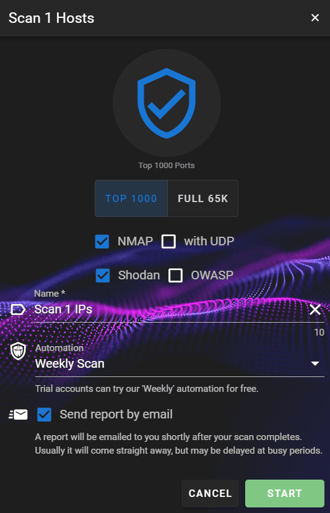
Step 3: Allow the scan to finish executing, this should only take a couple of minutes.
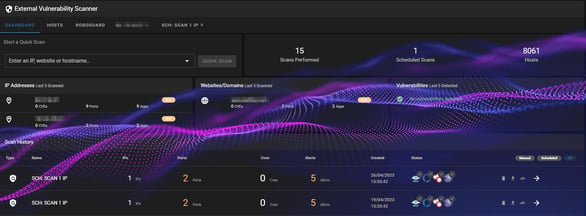
Step 4: Your report will now be generated, as well as other useful information, you should see a summary of open ports.
Step 5: Select the next arrow next to the scan to open the IP Dashboard
Step 6: You can now scroll through the list of open ports and decide which ones to investigate, by selecting the downwards arrow next to the open port.
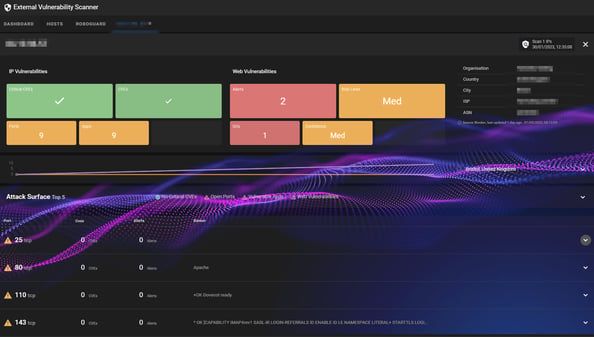
Investigating Open Ports
Once you've identified open ports on your network devices, it's crucial to determine their purpose. Querying open ports will provide you with more information about the services running on them. It will also help you assess whether they pose a security risk.
Here are some steps you can follow to query open ports:
- Identify the service. Review the scan results to determine the service running on an open port. Common services include HTTP, HTTPS, SSH, FTP, and SMTP. If you're unsure about a particular service, research it to understand its purpose and potential security implications.
- Check for known vulnerabilities. Search online resources for known threats associated with services running on open ports. Examples of such resources are the National Vulnerability Database (NVD) and the Common Vulnerabilities and Exposures (CVE) database.
- Inspect the device's configuration. Review the device's configuration settings to ensure that the open port aligns with its intended use. Pay special attention to access controls, encryption settings, and authentication mechanisms.
- Assess the necessity of the open port. Determine if the service running on the open port is essential for your network's operation. If not, consider closing the port or restricting access to authorized users only.
Securing Open Ports
Once you have identified the purpose of your open ports, here are some best practices to secure open ports:
- Close open ports. If an port is open, and is not required for your network's operation, close it to eliminate potential attack vectors. Block the connection to prevent access.
- Implement proper access controls. Restrict access to open ports or testing ports by using firewall rules, access control lists (ACLs), or other security mechanisms. Ensure that only authorized users and devices can access the services running on reserved ports.
- Update software and firmware. Regularly update software and firmware for all network devices to ensure that you have the latest security patches and fixes.
- Monitor and log activity. Use network monitoring tools and log management solutions to monitor and check ports for unusual or unauthorized activity. Regularly review logs to detect potential security threats.
- Conduct regular security audits. Perform periodic security audits to evaluate your network's security posture and identify potential threats. Use the findings to improve your security measures.
Thank You!
To keep your network safe, it's important to regularly check and protect any open ports on your devices. The steps explained in this blog can help you reduce the risks of cyber threats and safeguard your sensitive data. Remember that staying alert and adapting to new threats is an ongoing process in cyber security. By staying proactive and implementing strong security measures, you can greatly increase the strength and resilience of your network.
RoboShadow allows you to identify and query your external open ports for FREE.
Additional Resources
For further information and tools related to network security and open ports management, consider exploring the following resources:
I’m lucky to have worked in technology all over the world for large multi-national organisations, in recent years I have built technology brands and developed products to help make technology that bit easier for people to grasp and manage. By day I run tech businesses, by night (as soon as the kids have gone to bed) I write code and I love building Cyber Security technology.



