The main focus of the device vulnerabilities dashboard is to identify your most critical applications, along with the most vulnerable workstations, servers, and CVE vulnerabilities. Users have the option to either update or entirely remove these vulnerabilities from their devices and network Via Cyber Heal.
Additionally, businesses can address vulnerabilities on masse across their network using the Intune plugin. We've compiled this guide, accompanied by a video, to assist users in navigating the RoboShadow dashboard and strengthen their business's cybersecurity.
How to Install & Setting Up The Agent
Step One: Accessing the Agent
Navigate to the agent download section within RoboShadow.
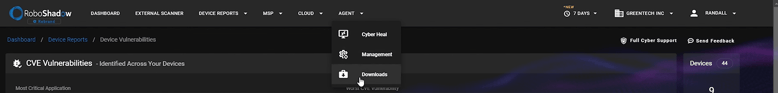
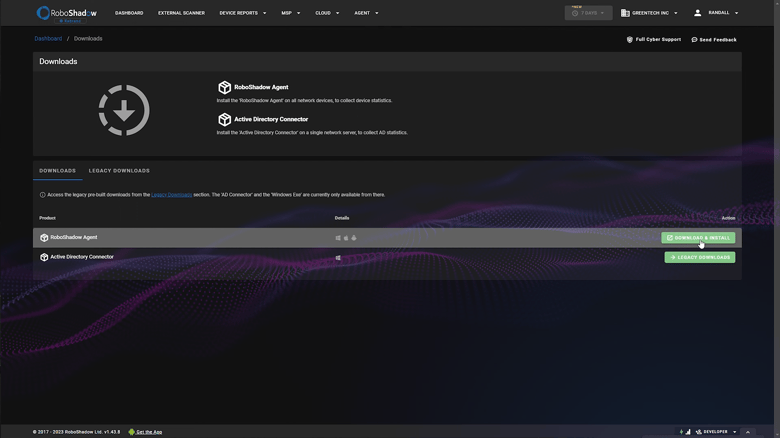
Step 2: Obtaining the Organization ID
Use the 'copy' function to acquire your organization ID, necessary for the following stage.
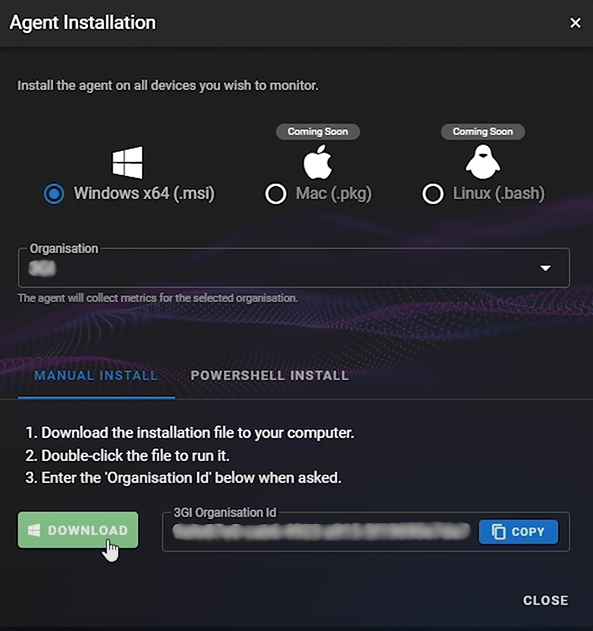
Step 3. Installing the Agent
During the installation process, you'll be prompted to input the organization ID.
Additional Features
- Automation Capabilities: For those who lean towards automated tasks, RoboShadow supports bulk operations using platforms such as Intune.
- Pricing Model: The agent comes with a free, read-only version.

Dashboard Overview
Upon successful agent setup you will be greeted by the following highlights within the report:
The Most critical application :
This represents the software or application within your infrastructure that is most susceptible to threats or has the highest number of vulnerabilities.
The Worst Server :
This metric identifies the server in your network that has the most vulnerabilities or is configured in a way that makes it most susceptible to potential threats.
The Worst Workstation :
This points to the individual computer or terminal that, compared to others, has the highest number of vulnerabilities or security misconfigurations.
The Worst CVE Vulnerability :
This refers to the most severe known vulnerability in your system as per the Common Vulnerabilities and Exposures (CVE) system. These are publicly disclosed vulnerabilities that have been cataloged and can be referenced by their unique identifier.
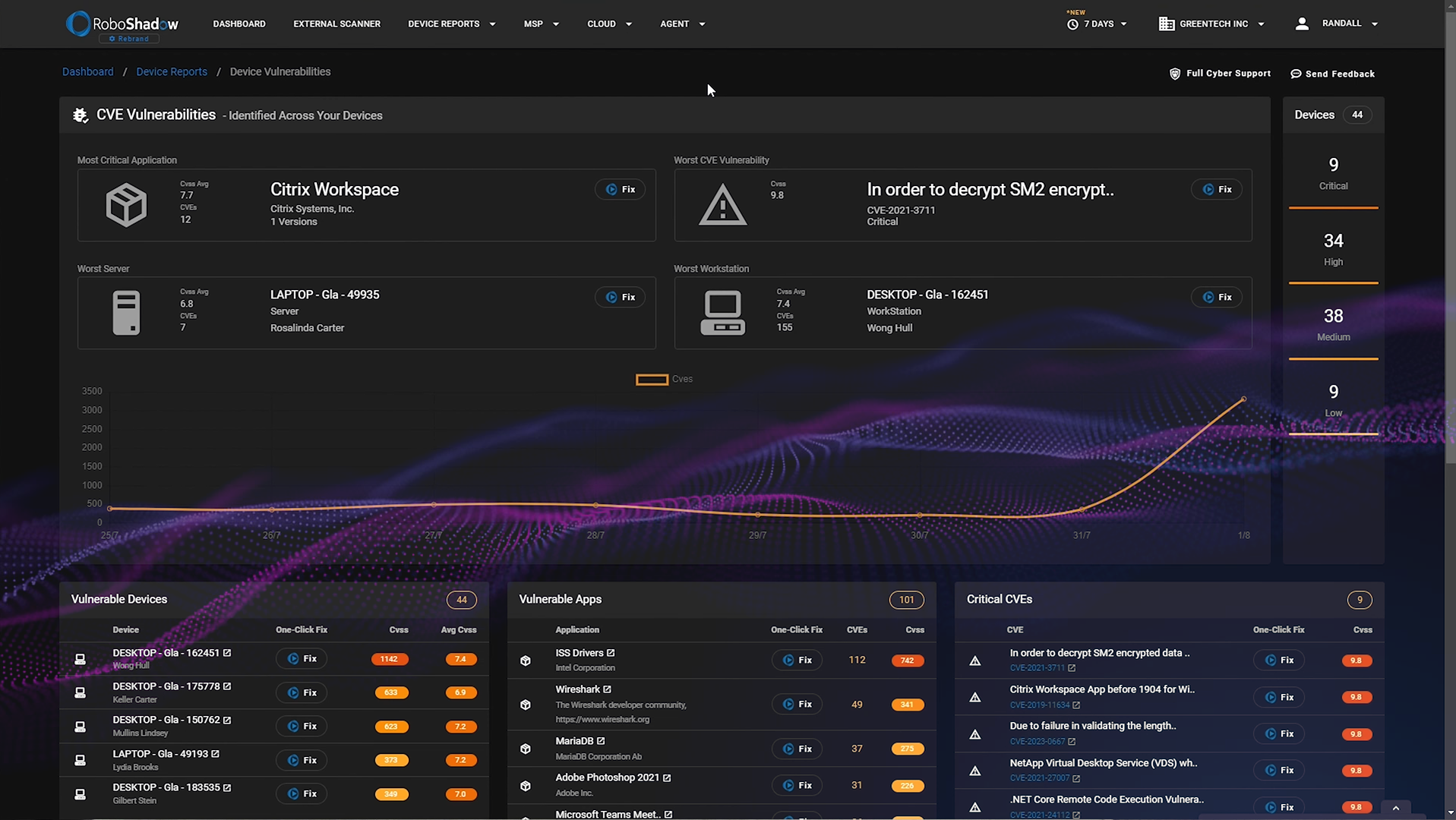
The dashboard displays lists of vulnerable devices, apps, and critical CVEs. You can use the Cyber Heal 'One Click Fix' feature in the 'Device Vulnerabilities' dashboard to address or eliminate these vulnerabilities.
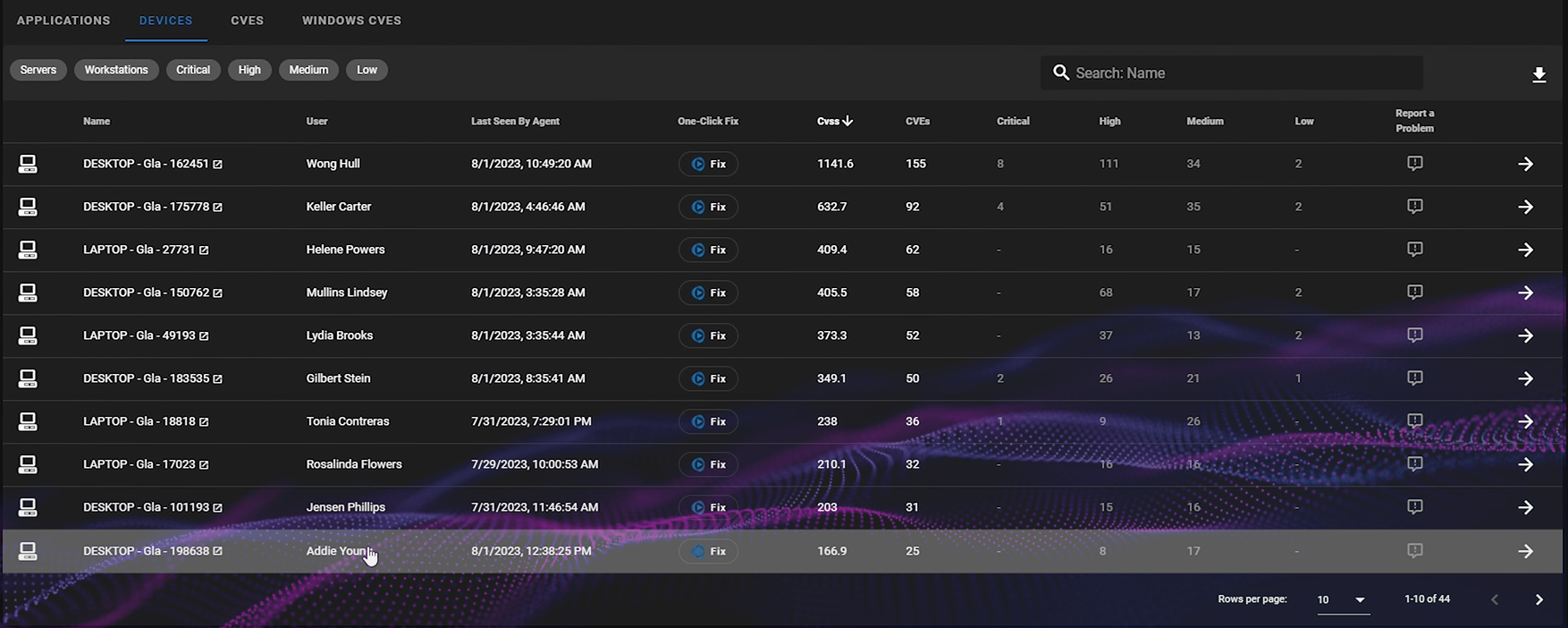 Discover which users are linked to at-risk devices.
Discover which users are linked to at-risk devices.
Remediation Recommendations
RoboShadow's platform extends beyond identification, and offers recommendations based on your data:
- Prescriptive Measures: Based on the nature and extent of the vulnerability, the dashboard may advocate for software updates or complete application removals.
- Application Risk Assessment: The system's focus isn't solely on high-risk applications; it evaluates reach. An app with moderate vulnerability but widespread use might be flagged for its broader potential impact.
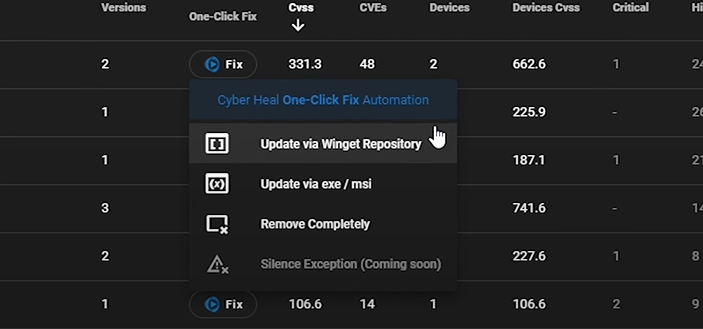
We also offer an additional premium feature called Cyber Heal, which allows you to remediate vulnerabilities within a single click. Cyber heal can also be used to install software under the winget repository onto multiple devices at the same time.
Cyber Heal enhances functionality, offering application updates through the 'Cyber heal One Click Fix' winget repository, XC, or MFSI files. It also allows for the complete removal of potentially unnecessary tools.
Any questions?
You can send us an email at hello@roboshadow.com. Additionally, for our current users, there's a convenient 'Support' option within the RoboShadow console, ensuring you get timely and effective responses. We're here to help and ensure your experience with RoboShadow is seamless and beneficial.








