One of the most common high risk failures we see on a good external penetration test is MFA / 2FA non-compliance. Multifactor authentication (MFA) or Two Factor Authentication (2FA) adds an additional layer of protection beyond user name and password, and Penetration Testers will mark accounts with no MFA enforcement on them as an external failure. A lack of MFA compliance means that your users are open to being easily externally phished without the hackers even having access to your network. Hackers could easily steal your user's identity.
Whilst most organisations will have rolled out MFA by now (and there are no excuses for any that haven't!) over time they can find that certain accounts (e.g. administrative, new users and remote access accounts) are given exceptions which snowball over time, leaving your system access vulnerable.
RoboShadow' s Free Tier allows you to complete an MFA Audit.
How to Perform A MFA Audit with RoboShadow
On the RoboShadow platform it's really easy to setup your MFA auditing capability and is part of the Free Tier. We are a Microsoft partnered entity, so we provide simple “one-click setup” with an account which has the correct permissions. This will then allow you to see your MFA status across all of your accounts and also what devices are not being tracked from a Cyber perspective with RoboShadow.
Step One:
Within the RoboShadow Portal, select 'Cloud' then 'Azure/365 MFA'.
Step Two:
Setup your Active Directory Synchronisation by selecting 'Configure AD Sync'.
Please note: You will need to have a Global Administrator account, as well as an Azure Active Directory Premium P2 license assigned to your Microsoft tenancy in order to complete this step.

Step Three:
Sign in to your global administrator account within the 365 portal.

Step Four:
You will now see a list of permissions that RoboShadow will need access to, click on 'Accept' if you are happy to proceed.

Step Five:
You will see a screen where it is syncing your AD. When this is complete, you will be able to select 'Return to Dashboard' to return to the MFA Audit page.
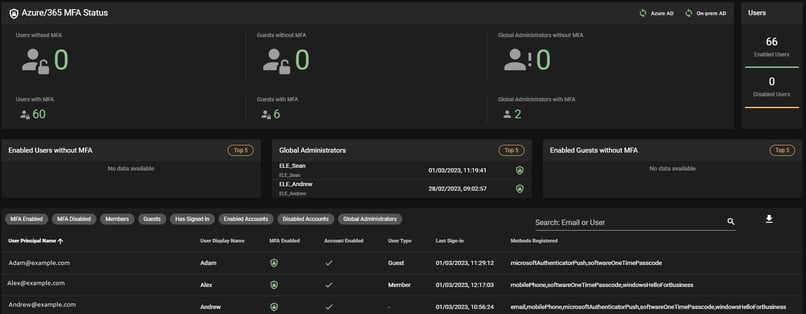
Step Six:
Once the sync is complete, you will then be able to track your users which don’t have MFA audit setup correctly, paying attention to the state of your global administrators.
Further Information
what is Multifactor Authentication (MFA) and how does it work?
Multifactor authentication (MFA) is a security process that requires two or more authentication factors to verify a user's identity. It typically involves something you know (password or PIN), something you have (security token) and something you are (fingerprint, retina scan). MFA adds an extra layer of security by making it harder for unauthorized users to access accounts and data, as each factor must be satisfied in order for the user to gain access.
One of the most common MFA used amongst our user community is Microsoft's inbuilt Multifactor Authentication, which is why we decided to include this as an audit point within the RoboShadow platform.

Why is MFA Compliance so important to Penetration Tests?
Penetration testers are looking to assess the security of your entire infrastructure, and will be marking any accounts which don’t have MFA enforced as a high-risk failure.
Hackers are becoming increasingly sophisticated, and having MFA enabled for all users is one of the most effective ways to protect yourself from attack because without MFA, hackers can easily phish credentials or steal identity in order to gain access to sensitive systems and data.
MFA provides an additional layer of security beyond user name and password, so having an audit process in place which checks whether your users have this enabled is essential.

How Can You Make MFA an Easier Experience For Users?
Users don’t always like having MFA enabled on their machines, as it means having to take an extra step before they can access required data. To alleviate this you can use Microsoft's Intune (Which is included in Microsoft 365 Business Premium!), then you can register the device with Intune so users don’t need to MFA each time. There are also ways of setting up conditional access to mark your office's IP address as safe.
This means that users will only need to MFA if they login to an unknown device or from a web browser that is not recognised. It can also help limit the need for multiple accounts.
Frictionless security is important for the user experience and operational efficiency.











