What is a CVE Vulnerability and why are they important?
If you look at any Vulnerability Scanning Tools available on the marketing (Including RoboShadow!) they will all include, at some point, references and data around CVEs. We look to explore CVEs in more detail, cover what they are and what to do when you find one.
So what even are CVEs?
CVE stands for Common Vulnerabilities and Exposures.
It is a catalog of publicly known information security threats, maintained by the non-profit MITRE Corporation. The MITRE Corporation's responsibility is to keep track of the latest threats and vulnerabilities, then assign each one with a CVE ID.
The CVE Database covers a wide range of cybersecurity threats, including those related to software vulnerabilities, network exposures, application weaknesses, malicious code attacks and more. CVEs are assigned unique identifiers which consist of the year of disclosure and an arbitrary number, e.g., CVE-2023-12345, to help track and reference known vulnerabilities.
CVEs are important because they provide a way to classify and keep track of all known vulnerabilities. This allows organizations and system administrators to quickly assess the risk level associated with a particular vulnerability, making it easier to prioritize security fixes and patches. Additionally, CVEs can be used as part of an organization’s overall security strategy when it comes to patch management. Having instant access to up-to-date information about potential threats makes it much easier for organizations to ensure their systems remain secure against emerging vulnerabilities or cyber risks.
Why are CVEs threats to organisations?
The biggest threat to organisations posed by CVEs is the potential for exploitation if left unaddressed. Unpatched software and vulnerable systems can be exploited for malicious purposes, ranging from data theft to fraud or worse. Additionally, these vulnerabilities may leave critical systems and infrastructure exposed to attack, leading to massive financial losses and reputational damage. Keeping track of CVEs is essential in order to ensure that organisations are aware of any security threats related to their systems and networks, so they can take steps towards protecting them.
To summarise, here are some of the biggest risks posed by CVEs:
- Easy ways in for bad actors , including hackers and malicious actors
- The potential for theft of sensitive data or disruption of service
- Unnecessary risks posed to critical systems and infrastructure
- Financial losses as a result of system downtime or data theft
- Reputational damage due to embarrassing public disclosure of security vulnerabilities
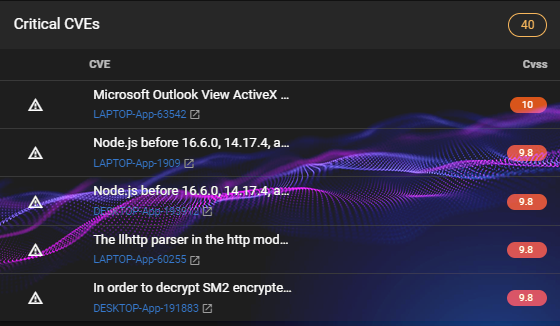
How to use a vulnerability scanner to scan for CVEs?
Having a reliable vulnerability scanner is the key to staying ahead of CVEs. A good tool will continuously monitor for new security threats and alert you when it finds them. It should also give you detailed reports that can help you quickly identify potential risks and take steps to mitigate them.
Two of the biggest vulnerability scanners on the market that also use CVE data to track vulnerabilities, such as Nessus. However, these tools can be expensive and require a lot of maintenance to stay up-to-date which means that for smaller organisations and charities, they can become too expensive or difficult to manage.
How can I detect CVEs for free?
Outside of expensive vulnerability scanners and tools, there are open-source alternatives like OpenVAS that can be used for free, although they may require more manual configuration and maintenance. Otherwise your only real option would be to spend endless time googling your different applications versions and any known vulnerabilities on them which is time your IT teams cannot afford.
At RoboShadow, we noticed that detecting vulnerabilities was something the industry puts a high price on, for something that is only a small amount of data! We believe this data should be available for free, so that everyone has a chance to improve their cyber security posture and find vulnerabilities within their system.
Within the RoboShadow platform, you can detect your open vulnerabilities for FREE using V-Scanner 2 which is hosted within our web application and connected to the CVE database. This means you can quickly and easily detect any vulnerabilities related to your installed software, without spending a fortune on expensive vulnerability scanners.
Alternatively, if you have the RoboShadow agent installed across your devices (Please click here for a guide!) you can track these also through Device reports > Device vulnerabilities to see a report of identified CVEs amongst your user base.
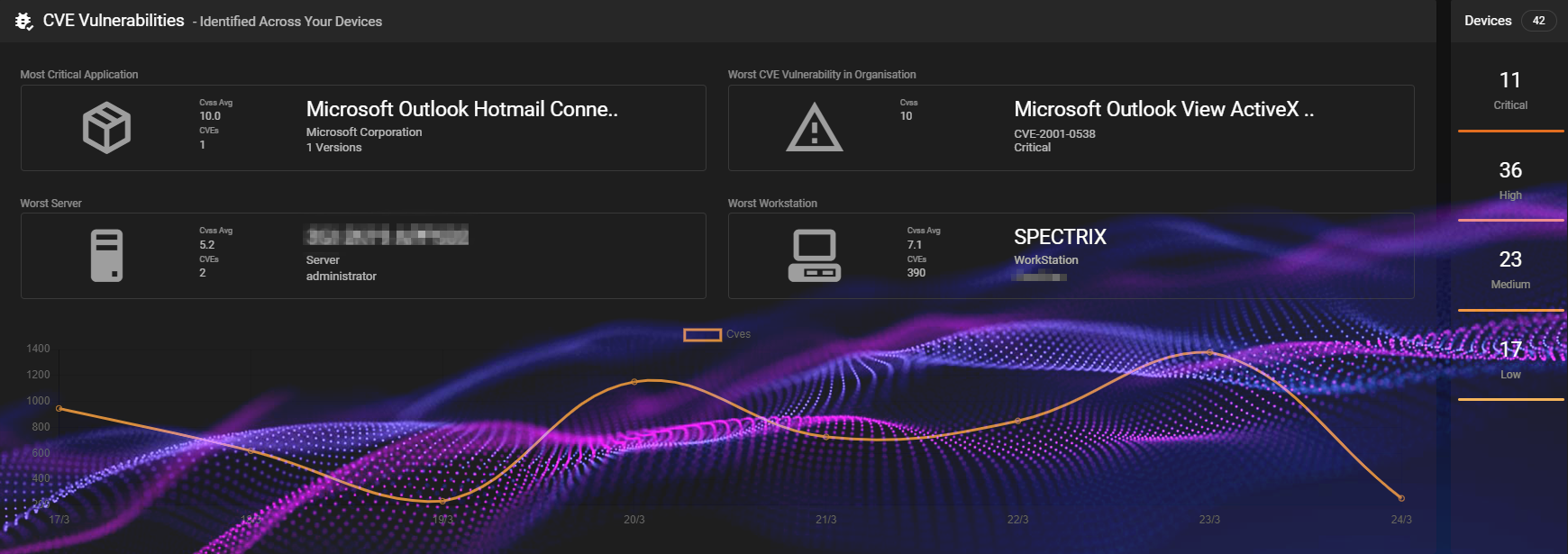
What should you do with CVE scan results?
Once you have identified potential vulnerabilities through scanning, the next step is to decide what action to take. It's important to remember that CVE entries indicate a problem and do not include technical data or detailed information about risks and impacts. However you could refer to the National Vulnerability Database (NVD) for additional information, such as Common Vulnerability Scoring System (CVSS) scores, which help assess the risk associated with each vulnerability.
When analysing the scan results of your vulnerability assessment, the vulnerabilities will be categorised based on their severity level. From there, you can create a prioritised list of actions. When prioritizing vulnerabilities, consider factors such as the CVSS score, the vulnerability's potential impact on your organization, and the ease of exploitation. Focus on remediating high-risk vulnerabilities first, as these pose the greatest threat to your organization.
may involve implementing security patches, upgrading software and hardware, or implementing additional security measures.
In RoboShadow, you can use our new (Beta) Cyber Heal feature to remediate your vulnerabilities using one click of a button.
In conclusion
CVEs present a risk to any organisation and it’s important to be aware of them. Using a vulnerability scanner is the best way to track these, however for smaller organisations and charities it can be too expensive or difficult to manage. At RoboShadow, we believe this data should be available for free.
I’m lucky to have worked in technology all over the world for large multi-national organisations, in recent years I have built technology brands and developed products to help make technology that bit easier for people to grasp and manage. By day I run tech businesses, by night (as soon as the kids have gone to bed) I write code and I love building Cyber Security technology.




